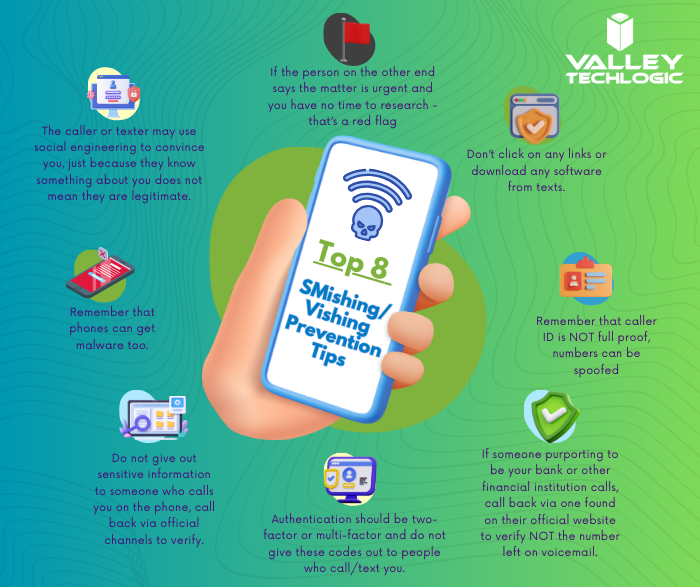
Intel just released a fix for a vulnerability that would make certain CPUs in jeopardy of being compromised. The vulnerability would allow an attacker to gain privileged access to machines or trigger a denial-of-service attack.
You can see the list of affected CPUs here, patching for this vulnerability may need to occur in phases including micro-updates to the BIOs, system OS and drivers. In a statement on their website Intel says malicious exploitation of this code would need execution of an arbitrary code (so it can’t be exploited with no input from the end user). They don’t believe patching for this issue will impact devices in a noticeable way.
Originally discovered by a Google Security Engineering team and dubbed “Reptar”, a researcher at Google commented on how strange this vulnerability appears to be.
The vulnerability changes how redundant prefixes, basically small bits of code, are interpreted by the effected CPUs. Normally CPUs ignore redundant prefixes for obvious reasons (the key word being “redundant”) but instead these prefixes triggered expanding errors within the system. The Google team found that when it was left without remediation eventually the affected machines would report processing errors and begin to malfunction.
Destructive code like this is frightening because it may not just be a loss of data or temporary use of the affected machine, but it may cause the computer or server to fail altogether.
This Isn’t the first CPU exploit Intel has suffered and they’re not the only ones battling attacks to their hardware, with AMD also announcing news of their own “CacheWarp” vulnerability that allowed attackers to gain root access to Linux Virtual Machines. So, if you thought these types of attacks were limited to Windows, think again. In this case the vulnerability only affects 1st through 3rd generation EPYC processors, the 4th generation is not vulnerable in this case.
Also, with the AMD vulnerability it’s also important to note that while a patch is available for just the 3rd generation EPYC processor. For 1st and 2nd generation there is no mitigation available. As with Intel it’s not expected that the patch will have any effect on the CPU performance.
Both companies have been very quick to patch these aggressive vulnerabilities and attacks like these highlight the need to make sure regular patching is a primary component of any tech service plan. Below are 5 key components we recommend when it comes to proactive technology support
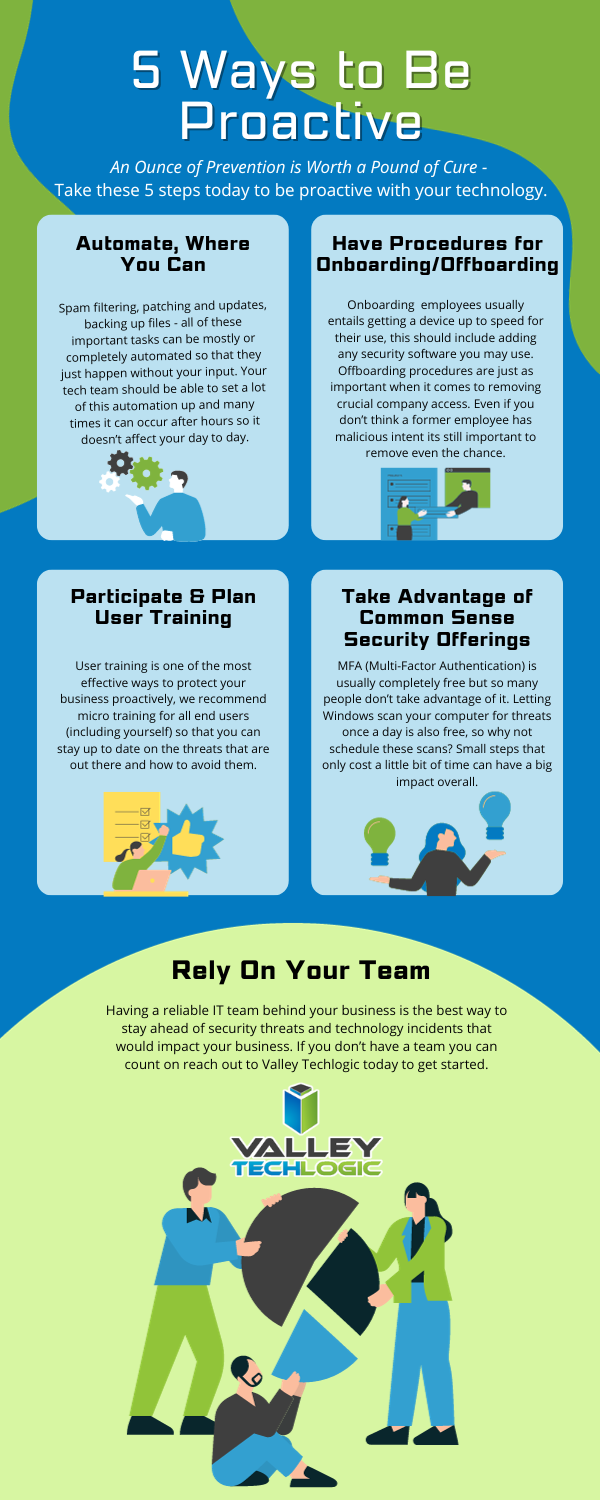 Proactive care is often a tough sell, with many business owners not feeling the need to spend the money on proactive tech care as these things “won’t happen to them”. It’s important to note that many attacks that occur are widespread and have no specific target in mind. If you have unpatched equipment in your office, you may be a sitting duck to any widespread attack issued to a vendor you use or because you bought a certain kind of hardware that ended up having a vulnerability. These attacks are ones of convenience not of malice as is often misconstrued.
Proactive care is often a tough sell, with many business owners not feeling the need to spend the money on proactive tech care as these things “won’t happen to them”. It’s important to note that many attacks that occur are widespread and have no specific target in mind. If you have unpatched equipment in your office, you may be a sitting duck to any widespread attack issued to a vendor you use or because you bought a certain kind of hardware that ended up having a vulnerability. These attacks are ones of convenience not of malice as is often misconstrued.
Even if it can be recovered from, why take the chance? Having a partner like Valley Techlogic to make sure vulnerabilities like the ones in this article are patched as soon as a fix is available means you will never be part of the eye-opening statistic about businesses who suffer a major breach. If you’re not aware, 60% of businesses close after a cyberattack. Don’t let that be you, reach out for a free consultation with us today.
Looking for more to read? We suggest these other articles from our site.
This article was powered by Valley Techlogic, an IT service provider in Atwater, CA. You can find more information at https://www.valleytechlogic.com/ or on Facebook at https://www.facebook.com/valleytechlogic/ . Follow us on Twitter at https://x.com/valleytechlogic.