If you’ve purchased a new laptop recently (or if you’re in the market) you may be wondering what to do with the fresh new start you now have on your hands.
However, there is the matter of your old laptop before you do anything with your new one, before you send it to e-waste or hand it off to the next person you want to make sure any files you’ll need now or in the future have been taken off of it and stored either directly onto your new device, into cloud storage, or even onto a portable hard drive. Once all of the files have been backed up and you can then safely wipe it to ensure no personal data remains (or have your IT team handle this if you’re unsure).
Now that the matter of your old laptop has been settled, we can move on to our five tips for maximizing your new laptops potential and setting it up as a new productive workspace:
- Perform Any Necessary Updates: Nothing is worse than getting settled in and ready to use a new device only to be prompted that you need to update RIGHT NOW. That’s why we suggest getting this out of the way and performing any necessary updates right out of the box, it may seem a little counterintuitive that a brand-new device would need updates right away but generally they’re packed up by manufacturers with just what you need to get it turned on – all the configuring comes later.
- Uninstall What You DON’T Want: This is also a good time to uninstall any pre-configured programs that you don’t want, like an anti-virus program that’s different than the one your company uses or programs that are really more of an advertisement for the manufacturer. Again, reach out to your IT team for assistance if you’re unsure what’s okay and not okay to remove.
- Set Up Backups for This New Device: If you’re using Microsoft 365 or Google Workspace your office probably has backups that would cover your new device, so you’ll want to set these up so any files you bring over or create on your new laptop are backed up as well.
- Install Your Productivity Software: Microsoft 365, Adobe, your preferred browser, applications for your VoIP provider, anything you need to do your job day to day can safely be installed at this point in the process.
- Finishing Touches: Lastly, you can setup your laptop in appearance, setting up dark mode where applicable, changing your background, setting your preferred font size. All the finishing touches that will make working from this new device feel streamlined and familiar (but with the added boost of having a newer, more capable device).
On the back end, your IT team should be setting up the tools needed to keep your new device safe such as end point protection, virus scans, malware detection and more. They may want to perform these updates right after any necessary updates to the operating system have been completed or they may want to as soon as your device will be connected to your office network. It’s a good idea to work with your IT team on setting up your new device in a way that’s both productive AND secure.
If you don’t currently have an IT team or the one you work with does not provide new device support, reach out to Valley Techlogic today. In addition to customized procurement advice and support, setting up new client devices is an included service in all of our support plans. Setup a consultation with us today to learn more.
Looking for more to read? We suggest these other articles from our site.
-
Six Ways Continuous Monitoring Keeps You a Step Ahead in Your Cyber Security Efforts
-
You have cloud backups for your business, but are you wasting money on storage you don’t need? 5 ways to tidy up your cloud storage
-
Apple releases their new M4 chip and it’s getting rave reviews, also considering the benefits of Apple vs Microsoft for your office
-
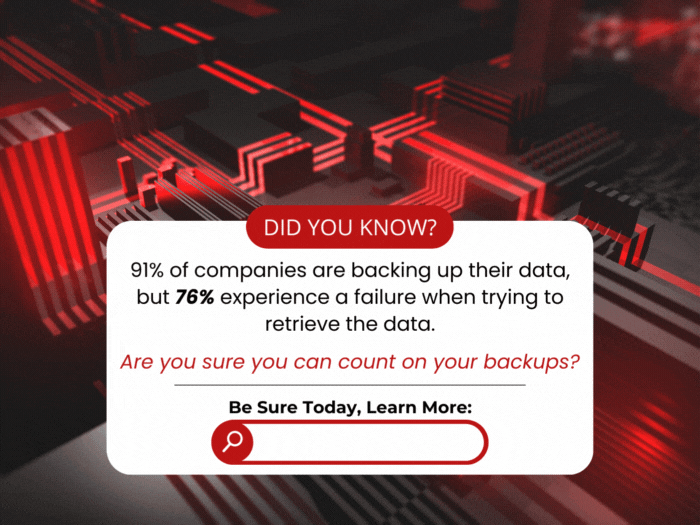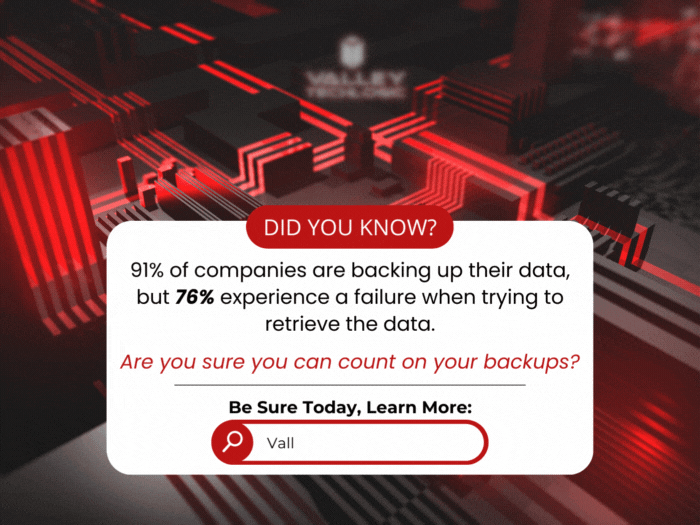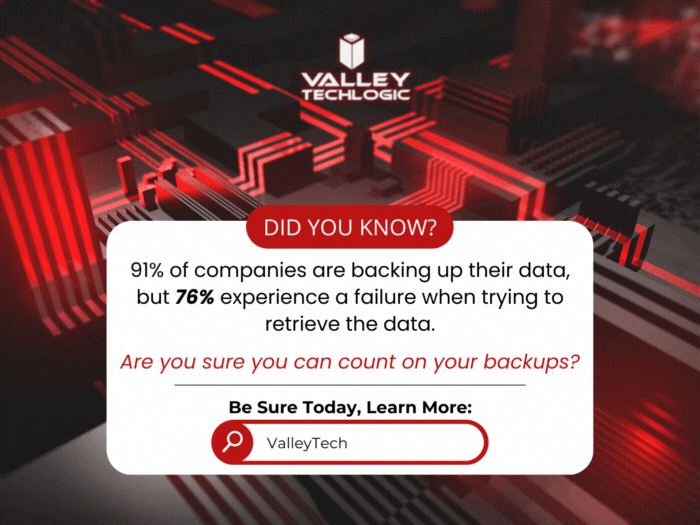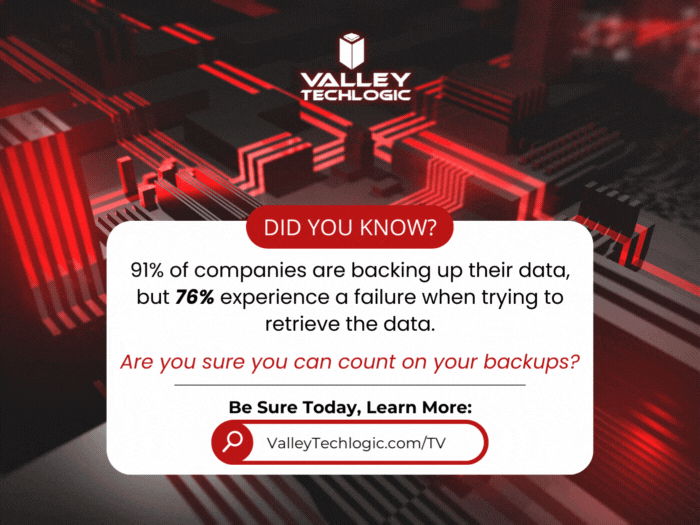
Are you sure you can count on your data backups? 5 ways to confirm your backups are working (and avoid the 37% data backup failure rate)
This article was powered by Valley Techlogic, leading provider of trouble free IT services for businesses in California including Merced, Fresno, Stockton & More. You can find more information at https://www.valleytechlogic.com/ or on Facebook at https://www.facebook.com/valleytechlogic/ . Follow us on Twitter at https://x.com/valleytechlogic and LinkedIn at https://www.linkedin.com/company/valley-techlogic-inc/.